Avoiding Escalation in Cyberspace

More on:
Brandon Valeriano is a Senior Lecturer at the University of Glasgow and Ryan C. Maness is a Postdoctoral Researcher at Northeastern University. They have recently published Cyber War versus Cyber Realities on Oxford University Press.
Restraint is the strategic underpinning of how many states confront cyber actions. Despite calls for a response to cyber aggression, the U.S. government still has not decided on a viable reaction given limited options. As David Sanger recounts in the New York Times, “in a series of classified meetings, officials have struggled to choose among options that range from largely symbolic responses … to more significant actions that some officials fear could lead to an escalation of the hacking conflict between the two countries.”
Strategic restraint tends to defy a form of conventional wisdom that sees the future of cyberspace as a lawless wild west where anything goes and offensive capabilities need to be built up in order to deter an adversary. This defines the tone of the New York Times story. In fact, some of the most cantankerous states in cyberspace tend to behave in a responsible manner because to act otherwise would invite terrible consequences.
Why do governments tend to not respond to cyber actions? According to our research, despite the massive influx of cyber operations that we are aware of we find little evidence of the escalation processes inherent in typical conflicts. In fact, we might be witnessing an era of cyberpeace. States operating in cyberspace react differently than in most strategic domains, a reality that drastically differs from perception given the way the news media reports the latest cyber violation as if it is the spark of a new onslaught and validation of the concept of cyberwar. There are two reasons for this: the dynamics of restraint and the development of cyber norms.
Restraint Dynamics
It’s easy to assume that the United States and other nations would “hack back” when their systems are targeted by adversaries. In fact, many private companies are moving towards this position after their networks are compromised. Yet government officials tend to understand something that private individuals do not: the inner workings of a bureaucracy are complex and dangerous. Needlessly provoking an escalatory response in a domain where both sides are wholly unprotected and borderline incompetent would be strategic suicide. For this simple reason we often see restraint. There is also the reality states will spy on each other, and sometimes even admire their adversaries’ work.
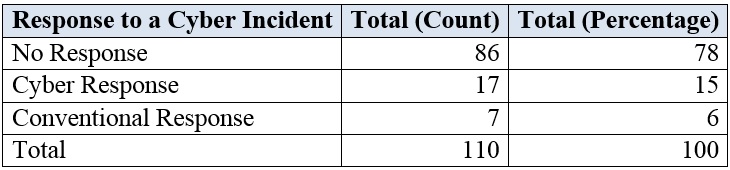
The U.S. government has so far refrained from responding to the OPM hack. If there is a response, we predict it will likely come through criminal charges on individuals, not the Chinese state. In fact, the great majority of cyber incidents in our data go without a response in the cyber or the conventional domains. A total of seventy-eight percent of cyber actions we code go without a counterstrike. Of those with responses, seventeen (fifteen percent) come in the form of a cyber response—with only two cases of escalation in severity—and seven conventional responses (six percent). The non-response is the typical response, by an overwhelming margin.
Building a System of Norms
The lack of escalatory activity can also be explained by a system of norms the United States and others seek to enforce in cyberspace. Like traffic laws, a basic understanding of how things work and what limitations exist benefit everyone. Of course there will be violators, but everyone needs to understand the rules of the road first. Even China and Russia appear to be willing to work within some system of norms, though they disagree with the United States on what the norms should be. Nevertheless, Russia and China are engaging in norms-setting institutions and process, such as the devolution of the Internet Corporation for Assigned Names and Numbers, recognizing that a rules-based framework is important to manage the growth of global connectivity.
While many may scoff at the idea of norms, they can be effective means to control the basic behaviors of the majority of actors. Of course there will always be deviants, but as long as we have clear systems of norms, deviancy will be seen as just that—out of the norm.
What Does the Future Hold?
This all bodes very well for our cyber future. While there is fear that the Internet will be primary threat vector for future societies, this alarmism is a bit premature and primarily based on the lack of understanding of how cyberspace works. We fear what we do not understand. Cyberspace can be controlled and made safe, but this requires us to understand it, to be aware of the possible escalation dynamics at hand in each conflict, and to be take in all available sources of information instead of relying on a few. Given the convergence of the basics of restraint and norms, even the most aggressive of states can be shown to be peaceful actors in cyberspace, even when being poked.
More on:
 Online Store
Online Store