New Entries in the CFR Cyber Operations Tracker: Q2 2024
An update of the Council on Foreign Relations’ Cyber Operations Tracker for the period between April and June 2024.
By experts and staff
- Published
Experts
![]() By Adam SegalIra A. Lipman Chair in Emerging Technologies and National Security and Director of the Digital and Cyberspace Policy Program
By Adam SegalIra A. Lipman Chair in Emerging Technologies and National Security and Director of the Digital and Cyberspace Policy Program
By
- Kyle FendorfResearch Associate, Digital and Cyberspace Policy
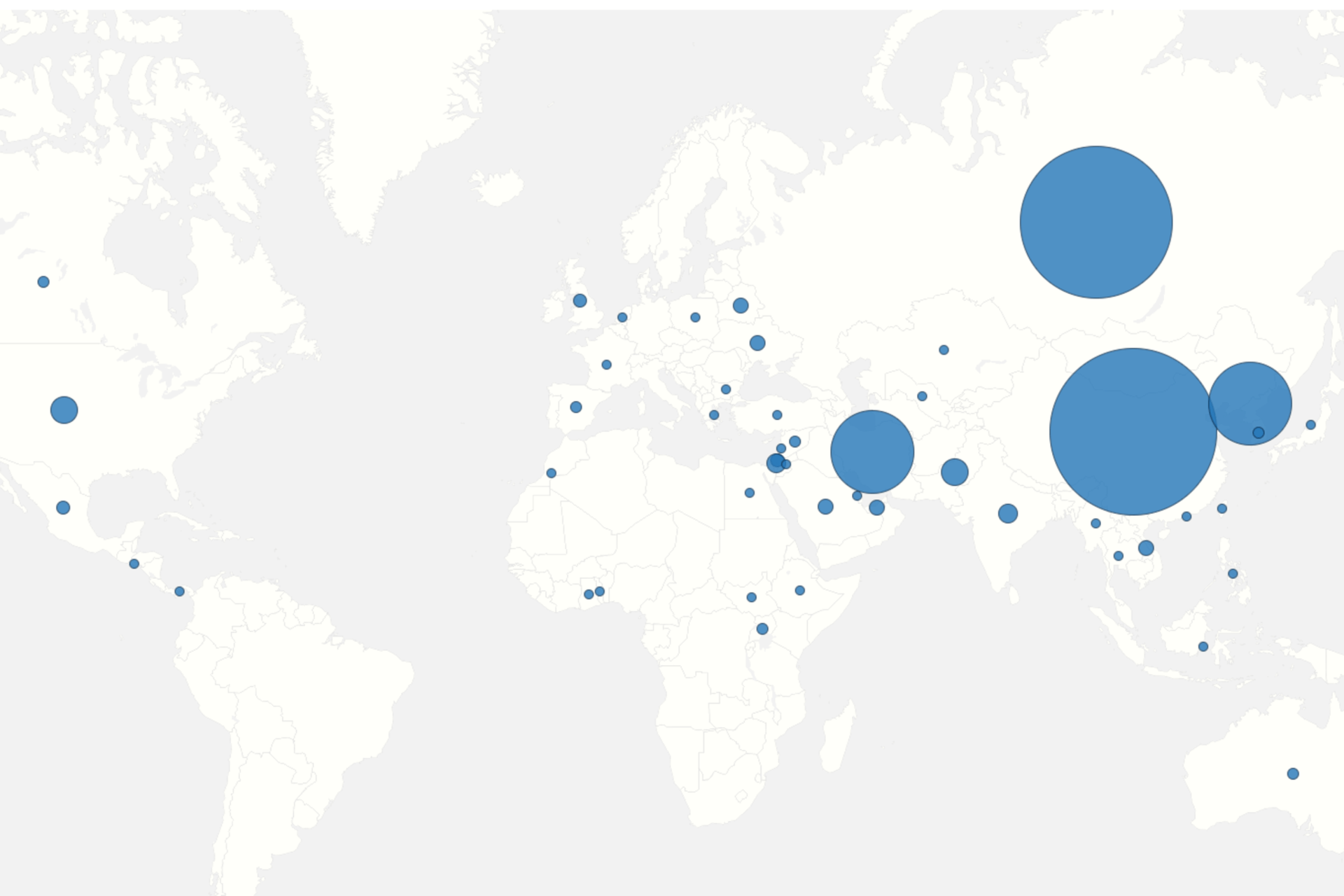
The Cyber Operations Tracker has just been updated. This update includes the state-sponsored incidents and threat actors that have been made public between April 1, 2024, and June 30, 2024.
A detailed log of the added and modified entries follows. If you know of any state-sponsored cyber incidents that should be included, you can submit them to us here.
Edits to Old Entries
Sandworm. Added affiliations with online cyber activist personas Xaknet, Cyber Army of Russia Reborn, and Solntsepek. Added update that Sandworm is associated with Telegram accounts which have taken credit for sabotage attacks on critical infrastructure in the U.S., France, and Poland.
Kimusky. Added affiliations. In addition to Thallium and Smoke Screen, also known as Emerald Sleet, TA-406, Sharptongue, Black Banshee, and APT43.
APT 36. Added that APT 36 has previously been observed targeting South Asian nations with a particular focus on government and military targets in Afghanistan and India.
New Entries
Incidents:
Actors:
Kyle Fendorf, research associate for the Digital and Cyberspace Policy program and Maya Schmidt, Digital and Cyberspace program intern, oversaw data collection.
