Eliminating a Blind Spot: The Effect of Cyber Conflict on Civil Society
Repressive regimes are increasingly adept at using digital espionage to suppress dissent and stifle opposition at home and abroad, even in democracies.

By experts and staff
- Published
By
- Guest Blogger for Net Politics
Lennart Maschmeyer is a PhD candidate at the University of Toronto and a fellow at the Citizen Lab and Columbia University’s School of International and Public Affairs. You can follow him @lenmaschmeyer.
Civil society organizations (CSOs) have been targeted by the same campaigns as large corporations and governments for over a decade, threatening not only freedom of expression but democracy itself. A prominent example is the 2009 Aurora campaign that compromised over thirty large corporations and became infamous for succeeding to steal Google’s source code. Less known was Aurora’s other main target: the Tibetan community. Since then, state-backed digital espionage has been increasingly used against journalists, activists, and humanitarian groups around the globe. Importantly, while facing the same advanced threats as large companies, CSOs lack resources to build up resilience and enlist outside help, rendering them highly vulnerable—and increasingly so as threats continue to evolve.
A new Citizen Lab report shows that the digital espionage threat against the Tibetan diaspora persists. It describes a targeted malware campaign targeting Tibetan activists, journalist, members of Parliament in exile and the Central Tibetan Administration. Despite the long history of digital espionage targeting the Tibetan community and other civil society movements, these experiences are largely ignored in debates about cyber conflict.
This situation underlines a worrying trend: repressive regimes are increasingly adept at using digital espionage to suppress dissent and stifle opposition at home and abroad.
Earlier this year, Columbia University’s School of International and Public Affairs held a workshop with Citizen Lab researchers to examine the digital threats facing civil society organizations, and the hurdles they encounter in mitigating them. Six challenges were identified.
First, there is a lack of standardized data about state-sponsored cyber operations. Academics have spent time and energy on speculating about cyber conflict, but much less on collecting and analyzing empirical data. Meanwhile, independent research centers like the Citizen Lab and nonprofits like the Electronic Frontier Foundation, Human Rights Watch, and Access Now have created an invaluable body of reporting on targeted threats to CSOs. These organizations contribute high quality research but their output is limited given funding and manpower constraints. The private cybersecurity industry is much better funded and collects enormous data on targeted threats, but it is driven by business interests that do not typically prioritize civil society.
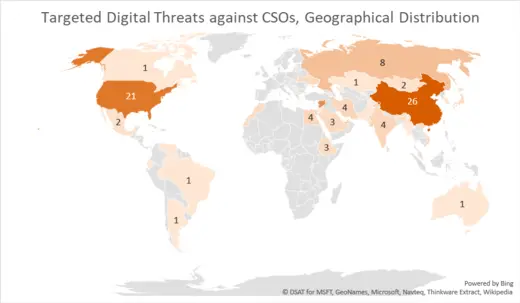
Second, targeted digital threats to CSOs are not a local problem limited to authoritarian countries, but a global threat as these regimes increasingly target civil society across borders. The following chart shows data from an analysis of public threat reporting by cybersecurity firms and independent research centers (paper in collaboration with Ron Deibert forthcoming). A significant proportion of threat activity targets CSOs in liberal democracies—with the second-largest share of reported threats to CSOs located in the United States, surpassed only by China. Since civil society is vital to a functioning democracy, the trend of authoritarian regimes projecting power abroad through digital means is an assault on democracy itself.
Third, technological development has created new opportunities for surveillance and espionage that evade existing regulatory and normative frameworks. Intelligence services and the private sector can exploit this grey area by supporting the development of new markets, such as the one for commercial spyware. While there is a legal case for lawful interception, accountability is challenging since these tools require secrecy to be effective. This puts civil society in peril, as illustrated by the controversies around spyware providers like FinFisher, Hacking Team and NSO Group selling capabilities on par with leading intelligence agencies to several authoritarian regimes.
Fourth, a misplaced focus on developing technological solutions when the majority of compromises in fact rely on social engineering techniques. While initiatives like the Vulnerabilities Equity Process (VEP) in the US are a potentially promising way to regulate disclosure of technical vulnerabilities, it misses the growing use of social engineering techniques that exploit vulnerabilities in behavior—such as curiosity, the human propensity to trust and socialize, and lack of care in opening email attachments. Regulating technology alone thus misses the majority of threats. In most attacks on civil society more effort is spent on effective social engineering used to trick targets into opening a malicious attachment or link rather than exploiting vulnerabilities in the technology itself, which is more expensive.
Fifth it is hard to quantify the effect of espionage on targeted CSOs, especially over the long-term. The effects of attacks on corporations and government agencies can be quantitatively measured in terms of financial losses and the amount of sensitive data being exfiltrated. Compromises affecting CSOs rarely result in financial damage, but rather arrests and persecution of the targeted individuals and their family members, as well as more long-term effects eroding trust within a community as individuals’ accounts are compromised and used to spread malware over social networks.
Sixth, there is no one-size-fits-all solution to mitigating the threat to CSOs. Each community is threatened and targeted differently. Tibetan diaspora organizations targeted by Chinese threat groups may face significantly different types of threats than Syrian opposition members targeted by both the regime and other non-state groups.
There are no easy answers to any of these challenges. Nevertheless, there are a few steps that grant-making organizations, policymakers, and tech companies could take to improve the cybersecurity of CSOs. First, grant-making organizations could provide more funding to conduct additional research on the threat to CSOs. Second, governments could call out countries that conduct cyber operations against civil society groups, analogous to what the Five Eyes and others did in calling out Russia over the NotPetya ransomware incident. They should also regulate the commercial spyware industry to curb its use against human rights advocates. Third, establishing increased accountability mechanisms for the commercial spyware industry to identify and curb the use of these products against civil society. Finally, private companies should develop strategies that increase the adoption of security features (such as multi-factor authentication) to raise the cybersecurity standard for targeted and vulnerable CSOs.