- Iran
- Israel-Hamas
-
Topics
FeaturedInternational efforts, such as the Paris Agreement, aim to reduce greenhouse gas emissions. But experts say countries aren’t doing enough to limit dangerous global warming.
-
Regions
FeaturedIntroduction Throughout its decades of independence, Myanmar has struggled with military rule, civil war, poor governance, and widespread poverty. A military coup in February 2021 dashed hopes for…
Backgrounder by Lindsay Maizland January 31, 2022
-
Explainers
FeaturedDuring the 2020 presidential campaign, Joe Biden promised that his administration would make a “historic effort” to reduce long-running racial inequities in health. Tobacco use—the leading cause of p…
Interactive by Olivia Angelino, Thomas J. Bollyky, Elle Ruggiero and Isabella Turilli February 1, 2023 Global Health Program
-
Research & Analysis
Featured
Terrorism and Counterterrorism
Violence around U.S. elections in 2024 could not only destabilize American democracy but also embolden autocrats across the world. Jacob Ware recommends that political leaders take steps to shore up civic trust and remove the opportunity for violence ahead of the 2024 election season.Contingency Planning Memorandum by Jacob Ware April 17, 2024 Center for Preventive Action
-
Communities
Featured
Webinar with Carolyn Kissane and Irina A. Faskianos April 12, 2023
-
Events
FeaturedJohn Kerry discusses his work as U.S. special presidential envoy for climate, the challenges the United States faces, and the Biden administration’s priorities as it continues to address climate chan…
Virtual Event with John F. Kerry and Michael Froman March 1, 2024
- Related Sites
- More
December 6, 2018
ChinaChina is once again conducting cyber-enabled theft of U.S. intellectual property to advance its technological capabilities. To combat the problem, the United States should build a multinational coali…

October 16, 2017
ChinaTo counter security threats of Chinese investment in U.S. critical technology, policymakers should boost innovation in the U.S. economy as a way to maintain a technological edge rather than seek to block or restrict Chinese investment or to limit the export of certain technologies.

October 16, 2018
CybersecurityDeep fakes—highly realistic and difficult-to-detect depictions of real people doing or saying things they never said or did—are a profoundly serious problem for democratic governments and the world order. A combination of technology, education, and public policy can reduce their effectiveness.
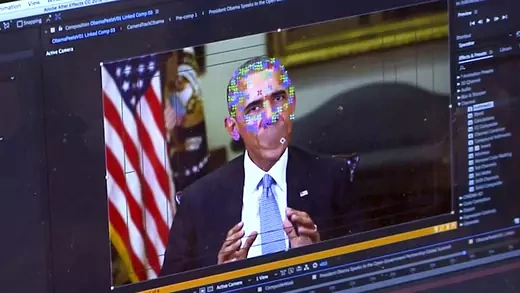
September 19, 2016
CybersecurityIn early 2016, the Federal Bureau of Investigation reportedly paid more than $1.3 million for a software flaw that allowed it to unlock an iPhone without Apple’s assistance. The purchase was possible…

July 27, 2020
United NationsAfrican UN member states should act as unifiers and conveners rather than dividers. More coordination could help them overcome the structural challenges they face at the United Nations.

 Online Store
Online Store