Chinese Investment in Critical U.S. Technology: Risks to U.S. Security Interests
Insights From a CFR Workshop

In July 2017, the Council on Foreign Relations’ Maurice R. Greenberg Center for Geoeconomic Studies held a workshop to explore the scale and scope of Chinese investment in U.S. technology, its national security implications, and potential policy responses. The workshop, hosted by then CFR Senior Fellow Jennifer M. Harris, was made possible by the support of the Carnegie Corporation of New York. The views described here are those of workshop participants only and are not CFR or Carnegie Corporation positions. The Council on Foreign Relations takes no institutional positions on policy issues and has no affiliation with the U.S. government.
Introduction
Chinese firms, both private and state-owned, have in recent years invested billions of dollars in the U.S. technology industry, raising concerns that a powerful rival has gained or could soon gain access to sensitive and, in some cases, critical technologies that underpin American military superiority and economic might. At the workshop entitled “Chinese Investment in Critical U.S. Technology: Risks to U.S. Security Interests,” held in San Francisco, on July 18, 2017, CFR convened nearly thirty current and former government officials, academics, bankers, investors, and corporate executives to explore whether the large and growing early-stage Chinese investment in critical U.S. technology poses a threat to U.S. national security, and, if so, to outline policies that mitigate the risks of unbridled Chinese investment and to bolster U.S. competitiveness.
Show Me the Money: The Scope of Chinese Investment in U.S. Technology
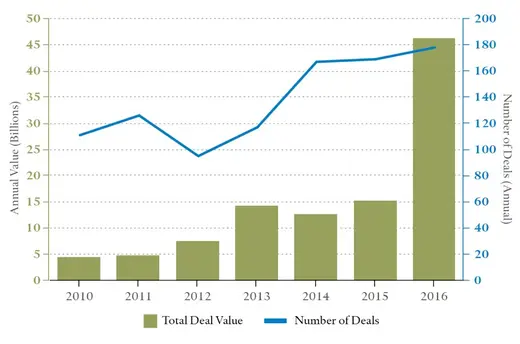
In 2016, Chinese investors, venture capital funds, and state-owned enterprises (SEOs) poured more money into all stages of U.S. technology development than ever before (see figure). This included acquisitions of not just established firms but also early-stage businesses and new initiatives from existing companies in nascent or newly developed technologies, in health and pharmaceuticals, in artificial intelligence (AI), and in other advanced technologies that could have cutting-edge military applications.
Participants largely agreed that, while most of the Chinese investments come from nominally private-sector firms, U.S. policymakers should view them as being made at the behest of the Chinese government, whether due to the availability of financing from state-owned banks or due to the Communist Party of China’s influence over significant private-sector companies. There is little functional distinction between private firms and SEOs, one participant noted; another underscored the role that Chinese state financing plays in lending a political overtone to what might otherwise appear to be private-sector investment decisions.
China’s Game: The Goals of Investing in U.S. Technology
Some participants argued that the investment flows are a natural extension of China’s decade-long quest to develop indigenous technologies to fuel economic growth: while Beijing once copied or simply stole technologies from advanced economies, now it is also buying them. Others pointed to Chinese economic plans—such as Made in China 2025, the Belt and Road Initiative, and China’s goal of reaching developed country status by the Communist government’s centennial in 2049—to argue that technology investments are being centrally directed toward concrete goals.
Other participants were more skeptical, pointing to what they described as a limited correlation between Chinese investment in U.S. technology and the Chinese government’s stated economic goals. Some investors could simply be chasing returns in the less-saturated U.S. market. Others underscored that a desire to get money out of mainland China could be driving “scattershot” investment across a range of U.S. economic sectors with minimal central direction or oversight. Or it could be a bit of everything at once; chasing returns, moving capital offshore, and meeting party goals are not mutually exclusive.
One participant summed up the difficulties in tracing and analyzing Chinese investment thus: “We know who is investing in whom. [But] we don’t know who owns them. And we don’t know why” they are investing.
Ultimately, participants concurred, while U.S. foreign direct investment in China still greatly exceeds Chinese investment in the United States, the playing field is “increasingly tilted” in favor of Chinese investors due to the essentially open nature of the U.S. economy. Though Chinese investors trying to purchase U.S. firms face low regulatory hurdles, the obstacles facing U.S. firms in China are much greater. U.S. banks operating in China, for instance, often cannot use the local currency; firms in other sectors face concerted challenges, from forced technology sharing to mandatory joint ventures, that foreign firms in the United States are not subjected to.
“We don’t enjoy free trade today,” one participant argued. “It’s only in one direction.”
Risks of Chinese Investment to U.S. Security
Several participants agreed that increased Chinese investment in new U.S. technology sectors could have two main national security implications: a direct threat to the U.S. military’s technological superiority, and, more broadly, an undermining of U.S. competitiveness in what one participant called the ongoing economic war with Beijing. Some participants, however, cautioned against exaggerating the potential threat posed by Chinese investment, particularly the risk of a return to a Cold War mentality.
The Department of Defense, in an unpublished 2017 report, has noted possible risks from Chinese tech investment to the so-called Third Offset, the U.S. military’s effort to ensure continued qualitative advantages over potential rivals, including China. The Third Offset—like its predecessors in the Cold War and through the post–Cold War period—seeks to both deter potential foes and reassure allies that the United States intends to maintain technological dominance over its rivals.
Extensive Chinese investment in sensitive technologies—such as guidance systems, AI, and light sensors that aid unmanned aviation systems—could erode or even eliminate that technological edge, some participants warned, potentially diminishing the United States’ ability to credibly defend allies, especially in Asia. Moreover, Chinese investment in high-tech firms could, in many cases, preclude U.S. government or military investment and cooperation with those same companies.

Beyond purely defense-related technologies, several participants stressed the risk that Chinese acquisition of novel technologies—especially in foundational technology such as AI that enables advances in a wide range of other areas—could ultimately undermine U.S. economic competitiveness. Some participants warned that Chinese access to precision data on genomics and pharmaceutical development could steal the mantle from U.S. companies currently dominating health care and related fields. Likewise, Chinese efforts to gain access to core communications and digital technologies could give Beijing the ability to harden its own cyber defenses while sharpening its cyberattack potential against the digital and telecommunications infrastructure of the United States and other countries.
The Third Offset: More Than Just Technology
Although potential threats to the U.S. military’s technological superiority dominated concerns about the implications of Chinese investment, some participants cautioned that the recent U.S. technological edge is a historical anomaly; therefore, the ending of this dominance would be a return to normality, not a revolutionary development.
Historically, few armies ever rode technological superiority to any lasting edge over their opponents, because most military technology, once encountered, is readily replicable, some participants noted. The introduction of the chariot, stirrup, firearms, automatic weapons, and armored vehicles were important but none remained dominant for long or conferred a lasting advantage.
The desire to keep a clearly superior technology secret and proprietary can erode all its advantages.
Instead, participants stressed, military doctrine, training, and operations are more reliable ways to ensure the ability to successfully wage war. A flexible command structure and battle-tested operational doctrines—rather than whizbang technology—provide a surer path to victory. Blitzkrieg was based not on superior technology—German tanks were initially lighter and weaker than their counterparts—but on doctrine and organization. Germany’s foes, especially the United States and the Soviet Union, copied much of that doctrine and organization in turning mobile tank warfare back against its creator.
Even when clearly a superior technology emerges, such as France’s development of the first true machine gun, the desire to keep the technology secret and proprietary can erode all of its advantages: the mitrailleuse conspicuously failed to win the Franco-Prussian War because it was too secret for the French troops to be trained in.
How the United States Should Respond
With respect to countering security threats from Chinese investment in U.S. critical technology, participants overwhelmingly preferred playing offense to defense: policymakers should boost innovation in the U.S. economy as a way to maintain a technological edge rather than seek to block or restrict Chinese investment or to limit the export of certain technologies.
To encourage innovation, many participants stressed the need for an industrial-competitive strategy in the United States, which would connect government and the private sector in planning, just as Chinese firms and their government coordinate. Some recommended institutionalizing public-private cooperation in the United States, while safeguarding free-market principles. Several cited the historical examples of government-funded and -directed basic research, epitomized by Bell Laboratories, as ways to ensure continued dominance of foundational technologies that ensure economic primacy.
However, nearly all participants also acknowledged that the current political climate makes such cooperation difficult. Budget pressures on basic government research already threaten the network of national labs. Meanwhile, populist rhetoric favoring defensive measures such as tariffs and blacklists makes it harder for policymakers to make the case that a more open economy is ultimately more resilient.
U.S. policymakers should make reciprocity a priority objective, and the United States has leverage over China to do so.
Participants vigorously debated how to bolster U.S. protections against Chinese access to critical technologies, including an expanded mandate for the Committee on Foreign Investment in the United States (CFIUS), targeted restrictions on critical technologies such as aeronautics and guidance systems that are vital to defense, and an insistence on Chinese reciprocity in investment and market access.
CFIUS, a government panel that screens foreign investment for possible national security implications, has for decades been the default tool to limit foreign access to sensitive parts of the U.S. economy. But many participants argued that CFIUS is outdated, under-resourced, and applies too narrow a definition of national security to be particularly useful in limiting either the extent or the impact of Chinese investment.
While a majority of participants agreed that CFIUS should be expanded, with added resources to handle an already large volume of cases, they contended that even a new and improved CFIUS would at best be a “piece of the pie” in dealing with Chinese investment in U.S. technology.
Similarly, participants noted that U.S. policymakers have struggled since the end of the Bill Clinton administration to limit Chinese access to potentially sensitive technologies, especially those that could have both civilian and military applications. Some participants argued that a more targeted approach, meant not to block all or most Chinese investment but just that in the most critical technologies—such as machine learning and AI—would mitigate the damage. However, other participants countered that the U.S. government is not well equipped to identify which specific technologies will be game changers or which could pose a future security threat, rendering such an approach useless and potentially counterproductive. Soviet acquisition of precision-guided missiles was ultimately enabled by ball bearing technology, for example, something no U.S. government agency foresaw.
Participants agreed that China has, in recent years, taken advantage of the traditionally open U.S. economy by investing freely in the United States while enforcing export controls and rigorously vetting investments and acquisitions on its shores. Most agreed that U.S. policymakers should therefore seek to make reciprocity—more equal access in China for U.S. investors, banks, and firms—a priority objective. And the United States currently has leverage over China to level the playing field. Participants differed, however, in how to do so. Some argued that privately urging China to open up would be more consistent with Chinese sensibilities, while others insisted that only by raising a “vocal stink” with Chinese authorities could unfair practices be rescinded.t





